WhatsApp has once again changed the algorithm to encrypt all the chat history messages saved on the SD card. This new encryption method is denoted by the .crypt7 filename extension.
To decrypt the crypt7 files, you will need two sets of decryption keys – the actual encryption key,K and an initialisation vector called IV . WhatsApp stores the keys in a file that is supposedly kept in a secure location.
|
1 |
/data/data/com.whatsapp/files/key |
Extract Key File
There are two ways to retrieve the file. For the first method, you will need a rooted phone. Using ADB shell, switch to root and copy the file to the SD card.
|
1 2 3 4 5 |
$ adb shell android$ su android# cp /data/data/com.whatsapp/files/key /sdcard android# exit android$ exit |
Once the file has been copied to the SD card, use ADB again to copy it to your computer.
|
1 |
$ adb pull /sdcard/key |
The second method to retrieve the file is to use the ADB backup feature. This requires your phone to be running on at least Android 4. Make a backup of WhatsApp data by running:
|
1 |
$ adb backup -f whatsapp.ab -noapk com.whatsapp |
This will cause a prompt on your phone as shown below. Click on the “Back up my data” button without providing a password.
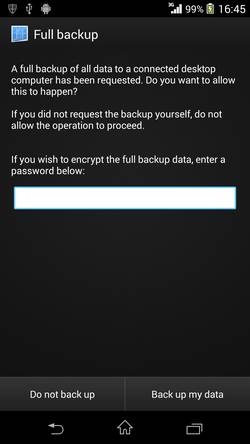
Once the backup has been completed, you will see a file called whatsapp.ab on your computer. The .ab extension stands for Android Backup. To extract files from the file, we will first need to convert it to a tar archive.
|
1 |
$ dd if=whatsapp.ab ibs=24 skip=1 | openssl zlib -d > whatsapp.tar |
Determine the key file location within the tar archive.
|
1 2 |
$ tar tvf whatsapp.tar | grep key -rw------- 10188/10188 158 2014-05-06 12:47 apps/com.whatsapp/f/key |
The key file is at “apps/com.whatapp/f/key“. Extract the key file and move it to the current working directory.
|
1 2 |
$ tar xf whatsapp.tar apps/com.whatsapp/f/key $ mv apps/com.whatsapp/f/key . |
Verify that the key file is exactly 158 bytes in size.
Extract crypt7 file
Pull the encrypted WhatsApp messages file from your phone using ADB.
|
1 |
$ adb pull /sdcard/WhatsApp/Databases/msgstore.db.crypt7 |
Extract Decryption Keys
The encryption method being used is AES with a key length of 256 bits and an initialisation vector size of 128 bits. The 256-bit AES key is saved from offset 0x7E till 0x9D in the file. Offsets start from 0x00. Extract the AES key with hexdump.
|
1 |
$ hexdump -e '2/1 "%02x"' key | cut -b 253-316 |
The above will give a 64-digit hexadecimal value in ASCII that is actually 256 bits in length.
Next, extract the IV or the initialisation vector.
|
1 |
$ hexdump -e '2/1 "%02x"' key | cut -b 221-252 |
The above will give a 32-digit hexadecimal value in ASCII that is actually 128 bits in length.
Strip Header in crypt7 File
Before we start the decryption process, we will need to strip the 67 byte header from the crypt7 file.
|
1 |
$ dd if=msgstore.db.crypt7 of=msgstore.db.crypt7.nohdr ibs=67 skip=1 |
The above command will strip the the first 67 bytes from the crypt7 file and save it to a file with extension crypt7.nohdr. If you look at the contents of the header, the IV value is actually stored there – between offset 0x33 till 0x42.
The file size of the header stripped file must be divisible by 128 bits or 16 bytes. For example, the size of my output file is 12660752 bytes – a number that is divisible by 16. If the file size is not in multiples of 16 bytes, then most probably your file is corrupted.
|
1 2 |
$ ls -l msgstore.db.crypt7.nohdr -rw-r--r--+ 1 ibrahim users 12660752 May 24 17:53 msgstore.db.crypt7.nohdr |
Decrypt crypt7 File
Now we have the necessary parameters to decrypt the crypt7.nohdr file using the openssl utility.
|
1 |
$ openssl enc -aes-256-cbc -d -nosalt -nopad -bufsize 16384 -in msgstore.db.crypt7.nohdr -K $k -iv $iv > msgstore.db |
Substitute $k and $iv with the AES encryption key and IV values that we retrieved using hexdump earlier. A non encrypted SQLite database file will be generated and saved to a file called msgstore.db.
Related: How to Extract Unencrypted Whatsapp Chat Messages
Related: Extract WhatsApp Password on Android

