Everyone knows that DNS is used to translate hostnames to IP addresses, but do you know that DNS can also be used to retrieve the domain name when the IP address is known?
I am not a DNS guru, but I do know that the ping command in Windows can be used to resolve IP addresses to hostnames by using the -a option.
|
1 2 3 4 5 6 7 8 9 10 11 12 |
C:\> ping -a 8.8.4.4 Pinging google-public-dns-b.google.com [8.8.4.4] with 32 bytes of data: Reply from 8.8.4.4: bytes=32 time=31ms TTL=50 Reply from 8.8.4.4: bytes=32 time=22ms TTL=53 Reply from 8.8.4.4: bytes=32 time=24ms TTL=50 Reply from 8.8.4.4: bytes=32 time=23ms TTL=50 Ping statistics for 8.8.4.4: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 22ms, Maximum = 31ms, Average = 25ms |
I had no clue how the reverse DNS query was performed by the ping command. To find out, I decided to analyse the DNS lookup query by using Wireshark, a network protocol analyzer. While trying to get the DNS name of the IP address of 8.8.4.4 (one of Google’s public DNS servers), I performed a packet capture.
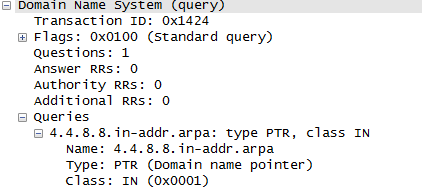
After some reading up, I managed to find out how reverse DNS lookup or reverse IP lookup works.
- The IP address is first reversed and the string
.in-addr.arpais added to the end of the IP address. So if the IP address is8.8.4.4, then the query becomes4.4.8.8.in-addr.arpa“ - The DNS query type is
PTR - The DNS query class is
IN
Now we have the necessary info to perform reverse DNS lookup. Now, let’s look at ways to perform reverse DNS lookups.
The first way is by using nslookup, a DNS query tool. The nslookup command is available in UNIX, Linux and Windows.
|
1 2 3 4 5 6 7 8 9 10 11 |
$ nslookup > set type=PTR > set class=IN > 4.4.8.8.in-addr.arpa Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: 4.4.8.8.in-addr.arpa name = google-public-dns-b.google.com. Authoritative answers can be found from: |
Is it too complicated? Fret not! There is another simpler way to do it using nslookup! Here you go:
|
1 2 3 4 5 6 7 8 |
$ nslookup 8.8.4.4 Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: 4.4.8.8.in-addr.arpa name = google-public-dns-b.google.com. Authoritative answers can be found from: |
Another DNS lookup utility commonly found in UNIX and Linux is the host utility.
|
1 2 |
$ host 8.8.4.4 4.4.8.8.in-addr.arpa domain name pointer google-public-dns-b.google.com. |
The final DNS lookup utility is called dig – a flexible tool for interrogating DNS name servers.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
$ dig -x 8.8.4.4 ; <<>> DiG 9.8.1-P1 <<>> -x 8.8.4.4 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 36351 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;4.4.8.8.in-addr.arpa. IN PTR ;; ANSWER SECTION: 4.4.8.8.in-addr.arpa. 85449 IN PTR google-public-dns-b.google.com. ;; Query time: 8 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Thu Mar 31 22:12:59 2011 ;; MSG SIZE rcvd: 82 |
If you are just interested in the answer section of the dig command output, append the +noall and +answer options to the dig command. Alternatively, you can use the +short option.
|
1 2 |
$ dig +noall +answer -x 8.8.4.4 4.4.8.8.in-addr.arpa. 85202 IN PTR google-public-dns-b.google.com. |

